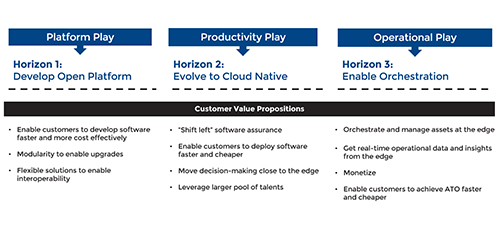
Lynx's Strategic Leap: Unveiling New Capabilities and Vision for Defense-Optimized Software Solutions
Strategic Expansions and Future Capabilities in MilAero Market In December, we unveiled Lynx’s acquisition of Timesys, our first major growth since OceanSound Partners acquired Lynx in June 2022....