LynxSecure: Separation Kernel Hypervisor
LynxSecure: Separation Kernel Hypervisor

BENEFITS OF LYNXSECURE
Our focus is on reducing program risk, development costs, and timelines. LynxSecure:
- Provides the simplest path to DO-178C DAL A certification for mixed criticality architectures
- Is a strong foundational element on which to create secure platforms that harness multicore processors
- Provides resiliency to cyberattack through unmodifiable allocation of system resources for each partition (“Least Privilege” model)

FUTURE-PROOFED, CYBER RESILIENT, DETERMINISTIC SOFTWARE PLATFORMS
LynxSecure is a simple and elegant platform technology that harnesses the hardware virtualization capabilities of modern multicore processors. It was designed to satisfy the strictest real-time, high assurance computing requirements used to regulate military and aerospace computing environments, such as NIST, NSA Common Criteria, NERC CIP and DO178C.
LynxSecure: Separation Kernel Hypervisor

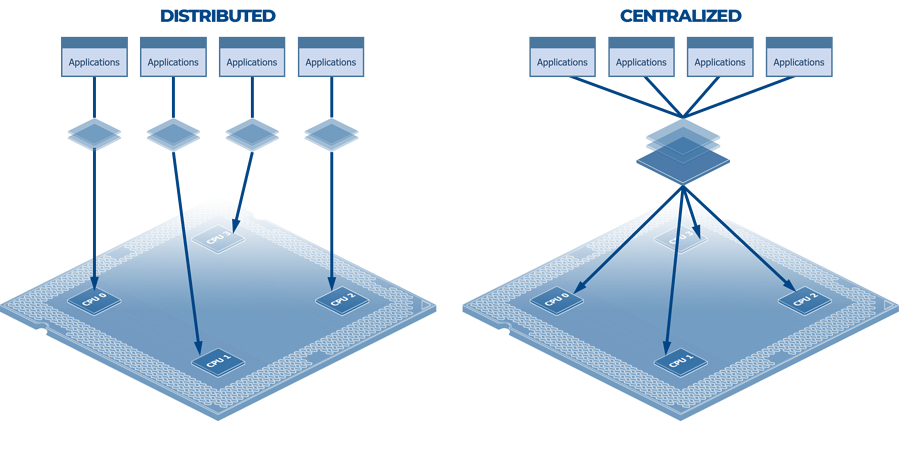
DISTRIBUTED VS CENTRALIZED
The separation kernel concept enforces a simpler distributed application runtime model on a processor by way of provably separating processor-controlled resources, such that independent applications execute on their own allocation of resources. With such a platform technology in place, the security properties of a software system can be verified by tracing system actors' data access and information flows directly to the physical allocation of resources:
Simply put, LynxSecure harnesses all of the functionality in the underlying platform, such as hardware virtualization, to ensure that each virtual machine will run independently and free of interference—from power on until power off. Additionally, LynxSecure offers advanced resource scheduling and security controls that exceed traditional operating systems and microkernel offerings. These LynxSecure tunables allow developers to explicitly define how a computer platform executes with traceable evidence from specification to instantiation, establishing platform integrity for design patterns that include:
• Safety and security domain isolation
• Trusted execution environments
• Reference monitor plugins such as firewalls and encryption
DEVELOPMENT BENEFITS
- Fastest path to DO-178C DAL A certification
- Creates safe, deterministic systems from multicore processors
- Designed from the ground up focused on delivering highest level of resiliency to cyberattack



















.png?width=250&height=86&name=Wabtec-Corporation-White-(1).png)