- Home
- Solutions
- Lynxmosaic
LYNX MOSA.ic™
The Foundation for Mission-Critical Edge Computing
MOSA.ic accelerates safety certification for secure multi-core systems through a modular separation-kernel architecture that enables deterministic partitioning, mixed-criticality consolidation, and open systems integration.



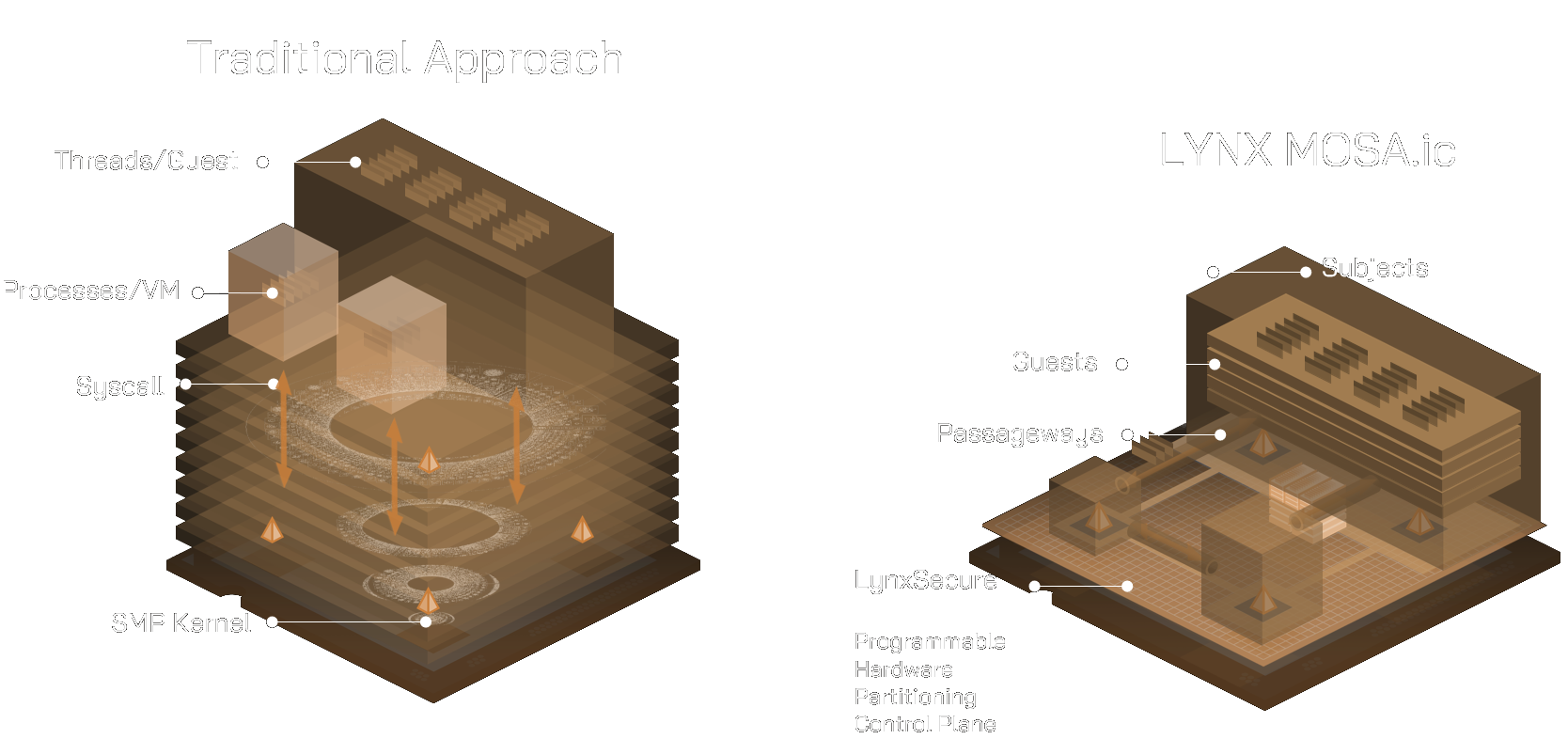
What is LYNX MOSA.ic?
LYNX MOSA.ic™ is a modular software framework and architecture purpose-built for mission-critical edge computing. Based on the Modular Open Systems Approach (MOSA), it provides a flexible foundation for building secure, scalable, and certifiable embedded systems.
Rather than relying on a traditional monolithic operating system, MOSA.ic uses a high-assurance separation kernel to securely run multiple operating environments side-by-side on a single multi-core processor. This includes support for a real-time operating system (RTOS) and a lightweight unikernel, enabling developers to match the right runtime environment to each application.
This architecture ensures that highly critical, real-time functions remain fully isolated from lower-priority software, even while sharing the same hardware delivering strong security, mixed-criticality support, and a clear path to certification.

Key Benefits
Accelerated Certification: By leveraging a modular architecture and tightly scoped, purpose-built components such as unikernels, MOSA.ic helps reduce overall certification effort and streamline recertification when changes are required, enabling faster time to deployment with lower program risk.
Optimized for Multi-Core Processors: Designed to take full advantage of modern multi-core architectures while aligning with CAST-32A and AC 20-193 guidance. Organizations can consolidate mixed-criticality workloads onto shared multi-core platforms with strong partitioning and controlled resource management that minimizes interference risk and supports robust safety arguments.
Future-Proof Modularity: Because the architecture is highly modular, individual software components can be updated, reused, or swapped out independently. This prevents vendor lock-in, reduces program risk, and makes legacy systems cost-effective to upgrade.
Core Architecture
The MOSA.ic software framework is powered by three foundational technologies designed for absolute security and determinism:

LynxSecure (The Hypervisor)

LynxOS-178 (The RTOS)

LynxElement (The Unikernel)
-1.png?width=857&height=875&name=image%20(14)-1.png)

Key Benefits
Accelerated Certification: By leveraging a modular architecture and tightly scoped, purpose-built components such as unikernels, MOSA.ic helps reduce overall certification effort and streamline recertification when changes are required, enabling faster time to deployment with lower program risk.
Optimized for Multi-Core Processors: Designed to take full advantage of modern multi-core architectures while aligning with CAST-32A and AC 20-193 guidance. Organizations can consolidate mixed-criticality workloads onto shared multi-core platforms with strong partitioning and controlled resource management that minimizes interference risk and supports robust safety arguments.
Future-Proof Modularity: Because the architecture is highly modular, individual software components can be updated, reused, or swapped out independently. This prevents vendor lock-in, reduces program risk, and makes legacy systems cost-effective to upgrade.
Did you know the LYNX MOSA.ic operating environment was selected by Bell to support the U.S. Army’s Future Long Range Assault Aircraft (FLRAA)?

Key Benefits
Accelerated Certification: By leveraging a modular architecture and tightly scoped, purpose-built components such as unikernels, MOSA.ic helps reduce overall certification effort and streamline recertification when changes are required, enabling faster time to deployment with lower program risk.
Optimized for Multi-Core Processors: Designed to take full advantage of modern multi-core architectures while aligning with CAST-32A and AC 20-193 guidance. Organizations can consolidate mixed-criticality workloads onto shared multi-core platforms with strong partitioning and controlled resource management that minimizes interference risk and supports robust safety arguments.
Future-Proof Modularity: Because the architecture is highly modular, individual software components can be updated, reused, or swapped out independently. This prevents vendor lock-in, reduces program risk, and makes legacy systems cost-effective to upgrade.
Who is it for?
MOSA.ic is designed for industries that cannot afford system failures
Aerospace
Defense
Industrial
Autonomous Mobility

Space
Works Across Multiple OSs and Platforms
Optimized for x86 and ARM architectures. While built around Lynx's core infrastructure, it seamlessly supports running Linux and other OS platforms in isolated partitions.


Enhanced Security Partnerships
Features immutable boot, automated CVE vulnerability management, and integration with 3rd parties such as RunSafe Security to deliver a memory-safe environment.
Watch: How Lynx and RunSafe are creating the first memory-safe RTOS
Download Whitepaper: Integrating RunSafe Protect with LYNX MOSA.ic


TSN Ready
Supports Time-Sensitive Networking (TSN) stacks for complex real-time networking needs.
In aerospace and defense, where systems must perform flawlessly and deliver data on time, TSN ensures the reliable network performance needed for these critical functions. Using LYNX MOSA.ic with TSN, you can connect all avionics systems, creating a safe and secure environment that meets the DAL A objectives of the DO-178C standard.


AI Ready
MOSA.ic, powered by CoreSuite, delivers an AI-ready architecture for mission-critical systems, securely consolidating safety-critical control and GPU-accelerated AI workloads on modern multi-core platforms.
Read blog: Modernizing the Mission Critical Edge without Breaking Assurance

Get in Touch
Deadlines and budgets are tight, and expectations are higher than ever. MOSA.ic ensures you deliver your system on time, on target, and ready for mission-critical success.